Install these tools using apt.
sudo apt-get install freeglut3-dev build-essential libx11-dev libxmu-dev libxi-dev libgl1-mesa-glx libglu1-mesa libglu1-mesa-dev
To avoid problems in driver installation process, you may want to put this on blacklist.
sudo nano /etc/modprobe.d/blacklist.conf
blacklist amd76x_edac blacklist vga16fb blacklist nouveau blacklist rivafb blacklist nvidiafb blacklist rivatv
Update/Install Nvidia card drivers
sudo apt-add-repository ppa:ubuntu-x-swat/x-updates sudo apt-get update sudo apt-get install nvidia-current
Download links: cuda-downloads
Cudatoolkit:
Make the cudatoolkit_4.2.9_linux_64_ubuntu11.04.run executable.
chmod +x cudatoolkit_4.2.9_linux_64_ubuntu11.04.run
Execute cudatoolkit_4.2.9_linux_64_ubuntu11.04.run.
sudo ./cudatoolkit_4.2.9_linux_64_ubuntu11.04.run
Software Development Kit:
Make the gpucomputingsdk_4.2.9_linux.run executable.
chmod +x gpucomputingsdk_4.2.9_linux.run
Execute gpucomputingsdk_4.2.9_linux.run
sudo ./gpucomputingsdk_4.2.9_linux.run
Pyrit:
wget http://pyrit.googlecode.com/files/cpyrit-cuda-0.4.0.tar.gz
tar xvzf cpyrit-0.4.0.tar.gz
cd cpyrit-0.4.0
python setup.py build
sudo python setup.py install
Error 1:
running build running build_py running build_ext building 'cpyrit._cpyrit_cpu' extension gcc -pthread -fno-strict-aliasing -DNDEBUG -g -fwrapv -O2 -Wall -Wstrict-prototypes -fPIC -I/usr/include/python2.6 -c cpyrit/_cpyrit_cpu.c -o build/temp.linux-x86_64-2.6/cpyrit/_cpyrit_cpu.o -Wall -DVERSION="0.3.1-dev (svn r278)" cpyrit/_cpyrit_cpu.c:37:18: error: pcap.h: No such file or directory
Solution: install libpcap-dev
sudo apt-get install libpcap-dev
Error 2:
/usr/local/lib/python2.7/dist-packages/cpyrit/cpyrit.py:63: UserWarning: WARNING: Version mismatch between module 'cpyrit._cpyrit_cpu' from '/usr/local/lib/python2.7/dist-packages/cpyrit/_cpyrit_cpu.so' ('0.4.0') and module 'cpyrit._cpyrit_cuda' from '/usr/local/lib/python2.7/dist-packages/cpyrit/_cpyrit_cuda.so' ('0.3.0')
"('%s')\n" % (_cpyrit_cpu, _cpyrit_cpu.VERSION, mod, ver))
Solution: remove this file then recompile
sudo rm /usr/local/lib/python2.7/dist-packages/cpyrit/_cpyrit_cuda.so
pyrit list_cores
Pyrit 0.4.0 (C) 2008-2011 Lukas Lueg http://pyrit.googlecode.com This code is distributed under the GNU General Public License v3+ The following cores seem available... #1: 'CUDA-Device #1 'GeForce 8600 GT'' #2: 'CPU-Core (SSE2)
pyrit benchmark
pyrit benchmark Pyrit 0.4.0 (C) 2008-2011 Lukas Lueg http://pyrit.googlecode.com This code is distributed under the GNU General Public License v3+ Running benchmark (1698.4 PMKs/s)... | Computed 1698.40 PMKs/s total. #1: 'CUDA-Device #1 'GeForce 8600 GT'': 1492.7 PMKs/s (RTT 2.8) #2: 'CPU-Core (SSE2)': 304.9 PMKs/s (RTT 2.9)
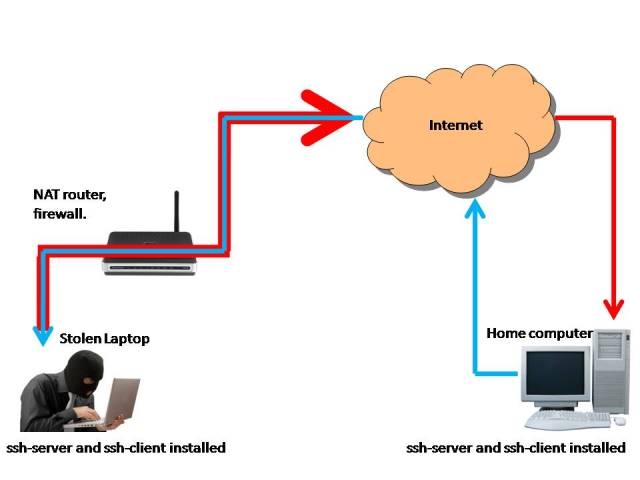
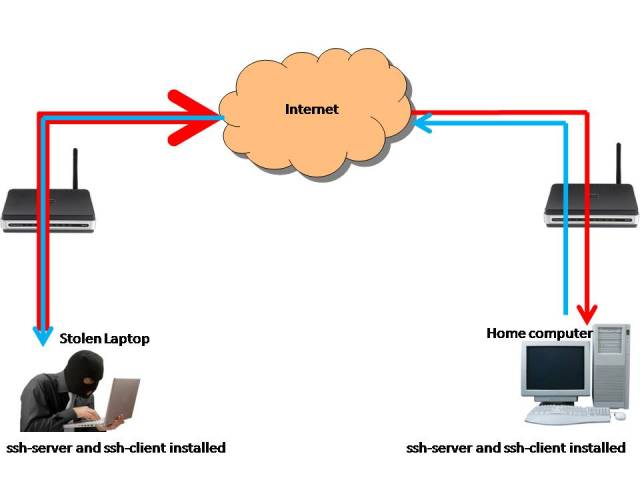
Unfortunately my laptop has no high-end GPU, I installed cpyrit on my desktop computer at home, ssh from my laptop will do when I’m away.